This section gathers our research results from most recent projects. Both important publications and experimental implementations can be found here.
| Date | Authors | Title | Conference/Journal | Link |
|---|---|---|---|---|
| 2024/07/30 | MALINA, L.; DOBIÁŠ, P.; DZURENDA, P.; SRIVASTAVA, G. | Quantum-Resistant and Secure MQTT Communication | ARES 2024 (SP2I) | ACM |
| 2024/07/30 | RICCI, S.; SHAPOVAL, V.; DZURENDA, P.; ROENNE, P.; OUPICKY, J.; MALINA, L. | Lattice-based Multisignature Optimization for RAM Constrained Devices | ARES 2024 (SP2I) | ACM |
| 2024/07/30 | MALINA, L.; DZURENDA, P.; LÖVINGER, N.; EKEH, I.; MATULEVICIUS, R. | Secure and Privacy-Preserving Car-Sharing Systems | ARES 2024 (SP2I) | ACM |
| 2024/07/10 | TŮMA, P.; HAJNÝ, J.; MUZIKANT, P.; HAVLÍN, J.; MALINA, L.; DOBIÁŠ, P.; WILLEMSON, J. | Open-Source Post-Quantum Encryptor: Design, Implementation and Deployment | Secrypt 2024 | Scirepress |
| 2024/03/05 | CÍBIK, P.; DOBIÁŠ, P.; RICCI, S.; HAJNÝ, J.; MALINA, L.; JEDLIČKA, P.; SMÉKAL, D. | Pushing AES-256-GCM to Limits: Design, Implementation and Real FPGA Tests | Applied Cryptography and Network Security (ACNS) | Springer |
| 2024/02/08 | RICCI, S.; DOBIÁŠ, P.; MALINA, L.; HAJNÝ, J.; JEDLIČKA, P. | Hybrid Keys in Practice: Combining Classical, Quantum and Post-Quantum Cryptography. | IEEE Access | IEEE |
| 2023/08/29 | MALINA, L.; DOBIÁŠ, P.; HAJNÝ, J.; CHOO, K. | On Deploying Quantum-Resistant Cybersecurity in Intelligent Infrastructures | ARES 2023 | ACM |
| 2023/08/29 | DANIDOU Y.; RICCI S.; SKARMETA A.; HOSEK J; ZANERO S.; LENDAK I. | DJM-CYBER: A Joint Master in Advanced Cybersecurity | ARES 2023 (ETACS 2023) | ACM |
| 2023/08/29 | DOBIAS P.; MALINA L.; ILGNER P.; DZURENDA P. | On Efficiency and Usability of Group Signatures on Smartphone and Single-board Platforms | ARES 2023 (SP2I 2023) | ACM |
| 2023/08/29 | BRIONES DELGADO A.; RICCI S.; CHATZOPOULOU A.; CEGAN J.; DZURENDA P.; KOUTOUDIS I. | Enhancing Cybersecurity Education in Europe: The REWIRE’s Course Selection Methodology | ARES 2023 (ETACS 2023) | ACM |
| 2023/07/12 | DOBIÁŠ, P.; RICCI, S.; DZURENDA, P.; MALINA, L.; SNETKOV, N. | Lattice-based Threshold Signature Implementation for Constrained Devices | SECRYPT 2023 | SCITEPRESS |
| 2023/06/08 | KIAC, M.; SIKORA, P.; MALINA, L.; MARTINÁSEK, Z.; SRIVASTAVA, G. ADEROS | Artificial Intelligence-Based Detection System of Critical Events for Road Security | IEEE Systems Journal | IEEE |
| 2022/11/01 | MALINA, L.; ŠEDA, P.; MARTINÁSEK, Z.; ŠROTÝŘ, M.; VANIŠ, M.; LOKAJ, Z.; POKORNÝ, J. | On Security and Privacy in Vehicle Speed Limiting Services in the Internet of Vehicles | IEEE Intelligent Transportation Systems Magazine | IEEE |
| 2022/10/31 | ROASCIO, G.; COSTA, G.; BACCELLI, E.; MALINA, L.; MATULEVICIUS, R.; MOMEU, M.; MORKEVICIUS, N.; RUSSO, E.; STOJANOVIC´, B.; TASIDOU, A. | HArMoNICS: High-Assurance Microgrid Network Infrastructure Case Study | IEEE Access | IEEE |
| 2022/09/07 | RICCI, S.; DZURENDA, P.; CASANOVA-MARQUÉS, R.; ČÍKA, P. | Threshold Signature for Privacy-preserving Blockchain | BPM 2022 | Springer |
| 2022/08/23 | HAJNÝ, J.; SIKORA, M.; DI FRANCO, F.; GRAMMATOPOULOS, A. | Adding European Cybersecurity Skills Framework into Curricula Designer | ARES 2022 (ETACS 2022) | ACM |
| 2022/08/23 | RICCI, S.; SIKORA, M.; PARKER, S.; LENDAK, I.; DANIDOU, Y.; CHATZOPOULOU, A.; BADONNEL, R.; ALKSNYS, D. | Job Adverts Analyzer for Cybersecurity Skills Needs Evaluation | ARES 2022 (ETACS 2022) | ACM |
| 2022/08/23 | LIESKOVAN, T.; HAJNÝ, J. | Security of Smart Grid Networks in the Cyber Ranges. | ARES 2022 (ETACS 2022) | ACM |
| 2022/08/23 | JEDLIČKA, P.; MALINA, L.; SOCHA, P.; GERLICH, T.; MARTINÁSEK, Z.; HAJNÝ, J. | n Secure and Side-Channel Resistant Hardware Implementations of Post-Quantum Cryptography | ARES 2022 (SP2I 2022) | ACM |
| 2022/08/23 | CASANOVA-MARQUÉS, R.; DZURENDA, P.; HAJNÝ, J. | Implementation of Revocable Keyed-Verification Anonymous Credentials on Java Card | ARES 2022 (SP2I 2022) | ACM |
| 2022/08/23 | DZURENDA, P.; CASANOVA-MARQUÉS, R.; MALINA, L.; HAJNÝ, J. | Real-world Deployment of Privacy-Enhancing Authentication System using Attribute-based Credentials | ARES 2022 (SP2I 2022) | ACM |
| 2022/07/13 | MALINA, L.; RICCI, S.; DOBIÁŠ, P.; JEDLIČKA, P.; HAJNÝ, J.; CHOO, K. | On the Efficiency and Security of Quantum-resistant Key Establishment Mechanisms on FPGA Platforms | SECRYPT 2022 | SCITEPRESS |
| 2021/11/02 | KAMAL, M.; TARIQ, M.; SRIVASTAVA, G.; MALINA, L. | Optimized Security Algorithms for Intelligent and Autonomous Vehicular Transportation Systems | IEEE TRANSACTIONS ON INTELLIGENT TRANSPORTATION SYSTEMS | IEEE |
| 2021/10/04 | RICCI, S.; DZURENDA, P.; HAJNÝ, J.; MALINA, L. | Privacy-Enhancing Group Signcryption Scheme | IEEE Access | IEEE |
| 2021/08/17 | HAJNÝ, J.; RICCI, S.; PIESARSKAS, E.; SIKORA, M. | Cybersecurity Curricula Designer | ARES 2021 (ETACS 2021) | ACM |
| 2021/08/17 | DZURENDA, P.; RICCI, S.; CASANOVA MARQUÉS, R.; HAJNÝ, J.; ČÍKA, P. | Secret Sharing-based Authenticated Key Agreement Protocol | ARES 2021 (SP2I 2021) | ACM |
| 2021/08/17 | RICCI, S.; MALINA, L.; JEDLIČKA, P.; SMÉKAL, D.; HAJNÝ, J.; CÍBIK, P.; DZURENDA, P.; DOBIÁŠ, P. | Implementing CRYSTALS-Dilithium Signature Scheme on FPGAs | ARES 2021 (main track) | ACM |
| 2021/08/17 | DZURENDA, P.; ANGLÉS, C.; RICCI, S.; MALINA, L. | Privacy-Preserving Online Parking Based on Smart Contracts | ARES 2021 (SP2I 2021) | ACM |
| 2021/08/17 | RICCI, S.; JANOUT, V.; PARKER, S.; JEŘÁBEK, J.; HAJNÝ, J.; CHATZOPOULOU, A.; BADONNEL, R. | PESTLE Analysis of Cybersecurity Education | ARES 2021 (ETACS 2021) | ACM |
| 2021/08/17 | LIESKOVAN, T.; HAJNÝ, J. | Building Open Source Cyber Range To Teach Cyber Security | ARES 2021 (ETACS 2021) | ACM |
| 2021/07/01 | HAJNÝ, J.; RICCI, S.; PIESARSKAS, E.; LEVILLAIN, O.; GALLETTA, L.; DE NICOLA, R. | Framework, Tools and Good Practices for Cybersecurity Curricula | IEEE Access | IEEE |
| 2021/06/06 | RICCI, S.; JEDLIČKA, P.; CÍBIK, P.; DZURENDA, P.; MALINA, L.; HAJNÝ, J. | Towards CRYSTALS-Kyber VHDL Implementation | SECRYPT 2021 | Scitepress |
| 2021/06/06 | CASANOVA MARQUÉS, R.; PASCACIO, P.; HAJNÝ, J.; TORRES-SOSPEDRA, J. | Anonymous Attribute-Based Credentials in Collaborative Indoor Positioning Systems | SECRYPT 2021 | Scitepress |
| 2021/05/25 | HAJNÝ, J.; DZURENDA, P.; CASANOVA MARQUÉS, R.; MALINA, L. | Privacy ABCs: Now Ready for Your Wallets! | IEEE PerCom 2021 | IEEE |
| 2021/05/22 | Farras O.; Ribes-Gonzales J.; Ricci S. | Privacy-preserving Data Splitting: A Combinatorial Approach | DESIGNS CODES AND CRYPTOGRAPHY | Springer |
| 2021/02/24 | MALINA, L.; DZURENDA, P.; RICCI, S.; HAJNÝ, J.; SRIVASTAVA, G.; MATULEVICIUS, R.; AFFIA, A.; LAURENT, M.; HAQUE SULTAN, N.; TANG, Q. | Post-Quantum Era Privacy Protection for Intelligent Infrastructures | IEEE Access | IEEE |
| 2021/02/04 | MALINA, L.; SMÉKAL, D.; RICCI, S.; HAJNÝ, J.; CÍBIK, P.; HRABOVSKÝ, J. | Hardware-Accelerated Cryptography for Software-Defined Networks with P4. | SecITC 2020/LNCS | Springer |
| 2021/02/04 | SAFONOV, Y.; MARTINÁSEK, Z.; MALINA, L.; PECL, D.; KAČIC, M.; ALMER, L. | Manager asks: Which vulnerability must be eliminated first? | SecITC 2020/LNCS | Springer |
| 2020/10/16 | SIKORA, P.; MALINA, L.; KIAC, M.; MARTINÁSEK, Z.; ŘÍHA, K.; PŘINOSIL, J.; JIŘÍK, L.; SRIVASTAVA, G. | Artificial Intelligence-based Surveillance System for Railway Crossing Traffic. | IEEE SENSORS JOURNAL | IEEE |
| 2020/01/20 | MALINA, L.; RICCI, S.; DZURENDA, P.; SMÉKAL, D.; HAJNÝ, J.; GERLICH, T. | Towards Practical Deployment of Post-quantum Cryptography on Constrained Platforms and Hardware-Accelerated Platforms. | Innovative Security Solutions for Information Technology and Communications (SecITC) | Springer |
| 2019/12/10 | MALINA, L.; SRIVASTAVA, G.; DZURENDA, P.; HAJNÝ, J.; RICCI, S. | A Privacy-Enhancing Framework for Internet of Things Services. | 13th International Conference on Network and System Security | Springer |
| 2019/09/17 | MALINA, L.; SRIVASTAVA, G.; DZURENDA, P.; HAJNÝ, J.; FUJDIAK, R. | A Secure Publish/Subscribe Protocol for Internet of Things | ARES 2019 | ACM |
| 2019/06/05 | HAJNÝ, J.; DZURENDA, P.; CAMENISCH, J.; DRIJVERS, M | Fast Keyed-Verification Anonymous Credentials on Standard Smart Cards | IFIP Advances in Information and Communication Technology | Springer |
| 2018/10/15 | MARTINÁSEK, Z.; HAJNÝ, J.; SMÉKAL, D.; MALINA, L.; MATOUŠEK, D.; KEKELY, M.; MENTES, N. | 200 Gbps Hardware-Accelerated Encryption System for FPGA Network Cards | ACM CCS ASHES | TBA |
| 2018/08/01 | MALINA, L.; DZURENDA, P.; HAJNÝ, J.; MARTINÁSEK, Z. | Secure and Efficient Two-factor Zero-knowledge Authentication Solution for Access Control Systems | COMPUTERS & SECURITY | Elsevier |
| 2018/08/01 | MALINA, L.; HAJNÝ, J.; DZURENDA, P.; RICCI, S. | Lightweight Ring Signatures for Decentralized Privacy-preserving Transactions | SECRYPT 2018 | SCITEPRESS |
| 2018/08/01 | HAJNÝ, J.; DZURENDA, P.; MALINA, L.; RICCI, S. | Anonymous Data Collection Scheme from Short Group Signatures | SECRYPT 2018 | ScitePress |
| 2018/07/29 | HAJNÝ, J.; DZURENDA, P.; MALINA, L. | Multidevice Authentication with Strong Privacy Protection | WIRELESS COMMUNICATIONS & MOBILE COMPUTING | Wiley/Hindawi |
| 2017/10/10 | DZURENDA, P.; RICCI SARA; HAJNÝ, J.; MALINA, L. | Performance Analysis and Comparison of Different Elliptic Curves on Smart Cards | 15th International Conference on Privacy, Security and Trust (PST) 2017 | UniCalgary |
| 2017/07/24 | DZURENDA, P.; HAJNÝ, J.; MALINA, L.; RICCI, S. | Anonymous Credentials with Practical Revocation using Elliptic Curves | SECRYPT 2017 | ScitePress |
| 2016/11/14 | MALINA, L.; HAJNÝ, J.; FUJDIAK, R.; HOŠEK, J. | On Perspective of Security and Privacy- Preserving Solutions in the Internet of Things. | Computer Networks | Elsevier |
| 2016/11/14 | MALINA, L.; HORVÁTH, T.; MÜNSTER, P.; HAJNÝ, J. | Security Solution with Signal Propagation Measurement for Gigabit Passive Optical Networks. | OPTIK | Elsevier |
| 2016/11/14 | MALINA, L.; HAJNÝ, J.; MLÝNEK, P.; MACHÁČEK, J.; SVOBODA, R. | Towards Efficient Application of Cryptographic Schemes on Constrained Microcontroller. | JOURNAL OF CIRCUITS SYSTEMS AND COMPUTERS | JCSC |
| 2016/11/14 | HAJNÝ, J.; DZURENDA, P.; MALINA, L. | Multi- Device Authentication using Wearables and IoT. | SECRYPT 2016. Lisbon, Portugal | TBA |
| 2016/11/14 | MARTINÁSEK, Z.; ZEMAN, V.; MALINA, L.; MARTINÁSEK, J. | k- Nearest Neighbors Algorithm in Profiling Power Analysis Attacks. | Radioengineering | TBA |
| 2016/10/24 | CAMENISCH, J.; DRIJVERS, M.; HAJNÝ, J. | Scalable Revocation Scheme for Anonymous Credentials Based on n- times Unlinkable Proofs | CCS WPES 2016, Vienna, AT | TBA |
| 2016/03/14 | OMETOV, A.; MAŠEK, P.; MALINA, L.; FLOREA, R.; HOŠEK, J.; ANDREEV, S.; HAJNÝ, J.; NIUTANEN, J.; KOUCHERYAVY, Y. | Feasibility Characterization of Cryptographic Primitives for Constrained (Wearable) IoT Devices | IEEE International Conference on Pervasive Computing and Communications (PerCom). 2016, Sydney, AU | TBA |
| 2015/11/01 | HAJNÝ, J.; DZURENDA, P.; MALINA, L. | Privacy-Enhanced Data Collection Scheme for Smart- Metering | INSCRYPT 2015, Beijing, China | Springer |
| 2015/10/30 | MALINA, L.; HAJNÝ, J.; ZEMAN, V. | Light-weight group signatures with time- bound membership | Security and Communication Networks | Wiley |
| 2015/08/01 | HAJNÝ, J.; MALINA, L.; DZURENDA, P. | Secure Physical Access Control with Strong Cryptographic Protection | SECRYPT 2015. Colmar, France | ScitePress |
| 2015/08/01 | MALINA, L.; MÜNSTER, P.; HAJNÝ, J.; HORVÁTH, T. | Towards Secure Gigabit Passive Optical Networks | SECRYPT 2015. Colmar, France | ScitePress |
| 2015/07/10 | HAJNÝ, J.; DZURENDA, P.; MALINA, L. | Attribute- based credentials with cryptographic collusion prevention. | Security and Communication Networks | Wiley |
| 2015/02/01 | MALINA, L.; HAJNÝ, J.; DZURENDA, P.; ZEMAN, V. | Privacy- preserving security solution for cloud services. | Journal of Applied Research and Technology | JART |
| 2014/11/14 | MALINA, L.; VIVES-GUASCH, A.; CASTELLA-ROCA, J.; VIEJO, A.; HAJNÝ, J. | Efficient Group Signatures for Privacy- Preserving Vehicular Networks | Telecommunication Systems | Springer |
| 2014/11/03 | HAJNY, J.; DZURENDA, P.; MALINA, L. | Privacy-PAC: Privacy-Enhanced Physical Access Control | CCS 2014, Scottsdale, USA | ACM |
| 2014/08/27 | HAJNY, J.; MALINA, L.; TETHAL, O. | Privacy-Friendly Access Control Based on Personal Attributes | IWSEC 2014, Hirosaki, Japan | Springer |
| 2013/11/27 | MARTINASEK, Z.; HAJNY, J.; MALINA, L. | Optimization of Power Analysis Using Neural Network | CARDIS 2013, Berlin, Germany | Springer |
| 2013/10/21 | Malina, L., Clupek, V., Martinasek, Z., Hajny, J., Oguchi, K., Zeman, V. | Evaluation of Software-Oriented Block Ciphers on Smartphones. | In Foundations and Practice of Security, FPS 2013, La Rochelle, France | Springer |
| 2013/09/12 | HAJNY, J.; MALINA, L.; MARTINASEK, Z.; TETHAL, O. | Performance Evaluation of Primitives for Privacy-Enhancing Cryptography on Current Smart-cards and Smart-phones | ESORICS DPM 2013, Egham, UK | Springer |
| 2013/08/31 | MALINA, L.; HAJNY, J. | Privacy-preserving framework for geosocial applications | Security and Communication Networks | Wiley |
| 2013/08/30 | MALINA, L.; HAJNY, J. | Efficient modular multiplication for programmable smart-cards | Telecommunication Systems | Springer |
| 2013/07/30 | MALINA, L.; HAJNY, J.; MARTINASEK, Z | Efficient Group Signatures with Verifier- local Revocation Employing a Natural Expiration. | Secrypt 2013, Reykjavik, Iceland | To be added |
| 2013/07/30 | HAJNY, J.; MALINA, L.; MARTINASEK, Z.; ZEMAN, V. | Privacy-preserving SVANETs | Secrypt 2013, Reykjavik, Iceland | SCITEPRESS |
| 2012/12/11 | HAJNY, J.; MALINA, L. | Unlinkable Attribute-Based Credentials with Practical Revocation on Smart-Cards | CARDIS 2012, Graz, Austria | Springer |
| 2012/10/02 | HAJNY, J.; MALINA, L. | Anonymous Credentials with Practical Revocation | Security and Privacy Special Track at the IEEE-AESS Conference in Europe about Space and Satellite Communications (ESTEL) | IEEE |
| 2012/10/25 | MALINA, L.; CASTELLA-ROCA, J.; VIVES-GUASCH, A.; HAJNY, J. | Short-term Linkable Group Signatures with Categorized Batch Verification | The Foundations & Practice of Security (FPS) Symposium 2012, Montreal, Canada | Springer |
| 2012/10/21 | MALINA, L.; HAJNY, J.; ZEMAN, V. | Group Signatures for Secure and Privacy Preserving Vehicular Ad Hoc Networks | The 8th ACM International Symposium on QoS and Security for Wireless and Mobile Networks, Paphos, Cyprus | ACM |
| 2012/09/03 | HAJNY, J.; MALINA, L. | Practical Revocable Anonymous Credentials | 13th Joint IFIP TC6 and TC11 Conference on Communications and Multimedia Security - CMS 2012, Canterbury, UK | Springer |
| 2011/18/18 | MALINA, L.; HAJNY, J. | Accelerated Modular Arithmetic for Low- Performance Devices | 34th International Conference on Telecommunications and Signal Processing, Budapest, Hungary | IEEE |
| 2011/07/18 | HAJNY, J.; MALINA, L.; ZEMAN, V. | Practical Anonymous Authentication: Designing Anonymous Authentication for Everyday Use | Secrypt 2011, Seville, Spain | DBLP |
| 2011/07/12 | HAJNY, J.; ZEMAN, V. | Anonymous Authentication with Spread Revelation | Cryptologia | Taylor & Francis |
Workshops
The 2nd SecTools workshop 2023
The second SecTools workshop is located at CVUT-FIT in Prague 18. 9. 2023.
The workshop program 11:30 – 15:00:
- Introduction and introduction of the participants.
- Presentation of project activities in 2023.
- Presentation of results and other activities.
- Presentation of activities in project stages:
1) Presentation of stages 11 and 12: Zdeněk Martinásek, Petr Jedlička BUT.
2) Presentation of stages 9 and 10: Petr Švenda MU.
3) Presentation of stages 7 and 8: Martin Novotný CVUT. - Afternoon program: discussion on SW analyzers with AG NÚKIB (Petr Švenda and Ján Jančár MU).
The presentations can be downloaded from the link (for the password please contact the project manager: Zdenek Martinasek at martinasek@vut.cz).
The 3rd SecTools workshop 2024
The second SecTools workshop is co-located with PQT workshop and SantaCrypt 2024 in Hotel Olympic in Prague 4. 12. 2024.
The workshop program 16:00 – 19:00:
- Introduction and introduction of the participants.
- Presentation of project activities in 2024.
- Presentation of results and other activities.
- Presentation of activities in project stages:
1) Presentation of stages 13 and 14: Martin Novotný CVUT,
2) Presentation of stages 18 and 19: Tomas Gerlich BUT.
3) Presentation of stages 15, 16 and 17: Petr Švenda MU. - Evening program: discussion with AG NÚKIB, project strategies (Petr Svenda, Jan Hajny, Lukas Malina).
The presentations can be downloaded from the link (for the password please contact the project manager: Zdenek Martinasek at martinasek@vut.cz).
Software List
- Software: Modular Arithmetic Library for .NET Cards
-
Software: Experimental Implementation of Modular Arithmetic Operations on the MultOS Smart Cards
-
Software: Secured Client – Server Messenger with Scalable Authentication
-
Software: Attribute Authentication Verifier for Smartphones
-
Software: Attribute Authentication Client for iOS
-
Software: DPA Contest v4 Attack
-
Software: Group Signatures Library
-
Software: IKE_PSK_SAM_v1
-
Software: libABC
-
Software: Android mobile application for access control system
-
Software: Smart Card Based Authentication Software
-
Software: Secure Access Module Based Authentication – Verifier Software
-
Software: Symmetric encryption on the FPGA card
-
Hardware cryptographic demonstrator
-
Cryptographic objects as externs in Netcope P4 compiler
-
Verification framework for user systems with integrated cryptographic P4 externs
-
Secure Cloud Storage System for Digital Evidence (CSDE)
-
Android mobile app for accessing a shared vehicle (IMA CARSHARING)
-
Software: Modular Arithmetic Library for .NET Cards
Authors
Ing. Lukas Malina (malina@vut.cz)
Ing. Jan Hajny (hajny@vut.cz)Download
It is possible to download the software (limited version) here.
Read more
Publication to be cited
MALINA, L.; HAJNY, J. Accelerated Modular Arithmetic for Low-Performance Devices. In 34th International Conference on Telecommunications and Signal Processing (TSP 2011). 2011 s. 1-5. ISBN: 978-1-4577-1409-2.
Project
The software (Modular Arithmetic Library for .NET Cards) was sponsored by the Technology Agency of the Czech Republic (project TA02011260).
Description
The implemented Modular Arithmetic Library provides basic mathematical operations such as addition, subtraction, multiplication, and exponentiation of large integers (from 0 to 1024 bits -limited version, to 2048 bits –full version) on the .NET Smart Cards. The library brings the missing arithmetic operations with large integers onto the .NET Smart Card platform that allows to build own algorithms which require modular arithmetic. The examples of such algorithms are advanced cryptographic schemes, anonymous authentication systems, etc. Also, the library includes an efficient algorithm for multiplication of large integers. The library (full version) uses advanced algorithms to achieve efficient multiplication of numbers in the range 0 to 2048 bitlength, see results in the related citation.
The graphical user interface (developed in C#/.NET 3.5) is used for testing and verification of implemented operations. You can test the time-performance of individual operations that are calculated by the library on a smart card using the implemented modular arithmetic algorithms. These methods within the library have a public access modifier, so the methods may be used by other applications.
In the package, you can find a test application with graphical user interface (Program.exe), and the compiled library implementation with modular arithmetic (Server.exe) which is ready to be imported on a smart card. For more detailed instructions about installation and operation see the Read Me document inside in zip file.
If you are interested in more info, please contact authors.
License
This software is licensed as closed source software under exclusive legal right of the copyright holder. The software is free for personal use only. For more information about the license, please contact:
Technology Transfer Office Brno University of Technology
E-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Software: Experimental Implementation of Modular Arithmetic Operations on the MultOS Smart Cards
Authors
Ing. Lukas Malina (malina@vut.cz)
Ing. Jan Hajny (hajny@vut.cz)Download
It is possible to download the software here.
Read more
Project
The software was sponsored by the Technology Agency of the Czech Republic (project TA02011260).
Description
This software consists of the main application with a graphical user interface and a test implementation of modular arithmetic operations running on MultOS cards. The test implementation is developed in C language, limited to the platform MultOS.
The main program (developed in Java) provides a user interface for communication with the chip cards, MultOS or JAVA. The aim is to provide middleware which ensures the communication between the card reader and chip card. The user can put data directly into the graphical user interface and display the results processed on the card. The main program is used as a handler for calling the methods of application that is imported on the Multos smart card. Either contact or non-contact smart cards are supported.
The application also offers testing of modular arithmetic operations on chosen MultOS cards. These operations running on the card are measured and the results are used as reference points for the further optimization of these operations run on the MultOS smart cards.
In this software package, you can find the main application with a graphical user interface (dir: dist Multos_M.jar) and two compiled test implementations in two versions for contact cards (dir: CARDC0) and non-contact cards (dir: CARDCL). The test implementation of attribute authentication is marked aa719. The test implementation of modular arithmetic is marked ma719. alu.
For both test implementations, individual certificates for loading (*.ALR) and deleting (*.ADR) are attached to the contact and non-contact card MultOS versions. To import a test implementation (alu), we recommend to download the freely available utility Mutil (http://www.multos.com/developer_centre/tools_and_sdk/), where you can import the *.alu along with the certificate *.ALR using the “load live”. For more detailed instructions about installation and operation, see document Read Me inside in zip file.
If you are interested in more info, please contact authors.
License
This software is licensed as closed source software under exclusive legal right of the copyright holder. The software is free for personal use only. For more information about the license, please contact:
Technology Transfer Office
Brno University of Technology
E-mail: info@tt.vutbr.cz
http://www.vutbr.cz/utt
Read less
Software: Secured Client – Server Messenger with Scalable Authentication
Authors
Ing. Lukas Malina (malina@vut.cz)
Ing. Zdenek Martinasek (martinasek@vut.cz)Read more
Project
The software was sponsored by the project FR-TI4/647.
Description
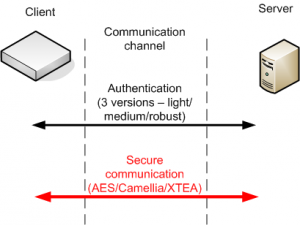
This
software provides the secure client-server transmission of messages,
the scalable authentication of entities (a client and a server), a
secret key establishment and the variable encryption of transmitted
data. The software is developed in JAVA and consists of two applications
with graphical user interfaces. The application Client represents a
client device (a remote PC, an external adapter, etc.) which is securely
connected to an integration server. Client can securely communicate
through the TCP / IP protocol. The application Server represents the
integration server that authenticates clients, collects income messages
and sends response messages. The software supports three protocols of
authentication: the light version (a HOTP method), the medium version (a
HOPT method and a key exchange via using asymmetric cryptography) and
the robust version (certificates and a key exchange via using asymmetric
cryptography).If you are interested in more info, please contact authors.
License
This software is used by TTC Telekomunikace s. r. o. as the result of
research project FR-TI4/647. For more information about the license,
please contact:Technology Transfer Office
Brno University of TechnologyE-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Software: Attribute Authentication Verifier for Smartphones
Authors
Ing. Lukas Malina (malina@vut.cz)
Ing. Jan Hajny (hajny@vut.cz)Download
It is possible to download the software (version 0.9) here.
Read more
Publication to be cited
[1]
HAJNY, J.; MALINA, L. Unlinkable Attribute-Based Credentials with
Practical Revocation on Smart- Cards. In Smart Card Research and
Advanced Applications. Lecture Notes in Computer Science. LNCS. Berlin:
Springer- Verlag, 2013. pp. 62-76. ISBN: 978-3-642-37287- 2. ISSN: 0302-
9743.
Project
The software was sponsored by the project FEKT-S-11-15.
Description
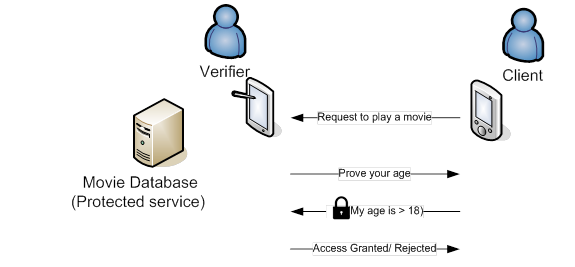
This
software consists of two applications, the Verifier and the Client. The
Verifier is the main application with a graphical user interface. The
software serves especially as a tool for a verifier entity in the
attribute authentication system [1]. The verifier can verify personal
attributes that serve as client’s authentication tokens to access a
service. Basic principle is depicted in Figure 1. Attribute
authentication systems allow the verification of individual clients
without any loss of their personal information. The full description of
the system and the proposed cryptographic scheme can be found in our
publication [1]. The software also contains the client application with a
graphical user interface developed on the Android platform.Figure 1. Use-case example of attribute authentication system.
The
verifier application provides three communication interfaces for the
authentication of clients. The communication interfaces are NFC
peer-to-peer communication, QR codes scanning and smart cards scanning
via NFC. The first communication interface provides the peer-to-peer
transmission of authentication attributes from the client to the
verifier via short NFC messages. This transmission is possible only if
the client uses a smartphone with a NFC module. NFC connection works
only for small distances (< 4 cm). The second interface allows a data
transmission using QR codes. This transmission is suitable for cases
where the client does not have a smartphone with NFC. The successful
transfer of QR codes depends on the quality of a camera (resolution,
zooming, …), and a good visibility between the camera and the display
with the QR code. The third communication interface scans chip cards
(smartcards) via NFC module.If you are interested in more info, please contact authors.
License
In case of interest in these applications, please contact authors.
This software is licensed as closed source software under exclusive
legal right of the copyright holder. The software is free for personal
use only. For more information about the license, please contact:Technology Transfer Office
Brno University of TechnologyE-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Software: Attribute Authentication Client for iOS
Authors
Ing. Jan Hajny (hajny@vut.cz)
Ing. Lukas Malina (malina@vut.cz)Download
It is possible to download the software (version 0.9) here.
Read more
Publication to be cited
[1] HAJNY, J.; MALINA, L. Unlinkable Attribute-Based Credentials with Practical Revocation on Smart- Cards. In Smart Card Research and Advanced Applications. Lecture Notes in Computer Science. LNCS. Berlin: Springer- Verlag, 2013. pp. 62-76. ISBN: 978-3-642-37287- 2. ISSN: 0302-9743.
Project
The software was sponsored by the project FEKT-S-11-15.
Description
The package contains the complete Xcode project of a client app that allows users to be anonymously verified as valid attribute holders. The app generates a QR code with necessary cryptographic values. The code is scanned and checked by the Verifier’s app.
If you are interested in more info, please contact authors.
License
The software is free for personal use only. For more information about the license, please contact:
Technology Transfer Office
Brno University of TechnologyE-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Software: DPA Contest v4 Attack
Authors
Ing. Zdeněk Martinásek, Ph.D. (martinasek@vut.cz)
Ing. Ondřej Zapletal
Ing. Lukáš Malina, Ph.D. (malina@vut.cz)Download
It is possible to download the software here.
Read more
Publication to be cited
[1]
MARTINÁSEK, Z.; HAJNÝ, J.; MALINA, L. Optimization of Power Analysis
Using Neural Network. In Smart Card Research and Advanced Applications,
Lecture Notes in Computer Science. Springer, 2014. s. 94-107. ISBN:
978-3-319-08302- 5.Project
The software
(DPA_Contest_attack) was sponsored by the Ministry of Industry and Trade
of the Czech Republic (project FR-TI4/647).Description
This
program realizes a power analysis attack for the DPA contest v4
(http://www.dpacontest.org/v4/index.php). Target implementation is a
masked AES-256 implemented in software on an Atmel ATMega-163 smart
card. This implementation is called AES-256 RSM (Rotating Sbox Masking).
Our implementation of the attack consists of two basic steps (see
Fig.1). In the first step, the secret offset of AES RSM is revealed by
MLP (Multi-Layer Perceptron) trained from power traces. In the second
step, the classical differential power analysis (DPA) based on a
correlation coefficient reveals a secret key stored in a cryptographic
device. A target intermediate value during DPA is the output of the
SubBytes function in the first round. The attack requires about 20 power
traces to obtain the secret key.In
the zip package, you can find an executable console application
(DPA_Contest_attack.exe), source m-files (one for linux and one for
windows) and an installation package. For more detailed instructions
about the installation and running of this program see the ReadMe.txt
document inside in the zip file.If you are interested in more info, please contact authors.
License
This
software is licensed as the closed source software under the exclusive
legal right of the copyright holder. The software is free for personal
use only. For more information about the license, please contact:Technology Transfer Office
Brno University of TechnologyE-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Software: Group Signatures Library
Authors
Ing. Jan Hajny (hajny@vut.cz)
Ing. Lukas Malina (malina@vut.cz)
Ing. Petr Dzurenda
Martin Jaros
Lukas PohankaDownload
It is possible to download the library (limited version) here.
Read more
Publication to be cited
[1]
HAJNÝ, J.; DZURENDA, P.; MALINA, L. Privacy-Enhanced Data Collection
Scheme for Smart-Metering. In Proceedings of the International
Conference on Information Security and Cryptology. Lecture Notes in
Computer Science. 2015. p. 1-18. ISSN: 0302-9743.Project
The software was sponsored by the Technology Agency of the Czech Republic (project TA03010818).
Description
The
software library (libGS) written in the C language enables the
calculation of the group signature and its verification (demo version).
Group signatures ensure data security, nonrepudation and also protects
the privacy of signers. The library is suitable for use on both sides
the client (the device) and the server side. The public API of the full
version provides the following functionality: the assignment of system
parameters of the defined values, generating client and server parts of
the private key (the key has 2 parts), the generation and validation of
group signatures and generating the revocation token.If you are interested in more info, please contact the main author (hajny@vut.cz).
License
The software is free for personal use only. For more information about the license, please contact:
Technology Transfer Office
Brno University of TechnologyE-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Software for authentication module using the protected storage IKE_PSK_SAM_v1
Authors
Ing. Lukáš Malina, Ph.D. (malina@vut.cz)
Ing. Zdeněk Martinásek, Ph.D. (martinasek@vut.cz)Download
It is possible to download the demo version here.
Read more
Publication to be cited
TBA
Project
The software (IKE_PSK_SAM_v1) was sponsored by the Ministry of the Interior of the Czech Republic (project VI20162018036).
Description
The
main features of the software is to verify the authenticity of the data
by using a pre-shared secret key on a smart card programmable and
provide the calculation of the encryption keys for the IPSec protocol.
Smart card hosts critical operations and secret parameters. These
operations are performed in this secure storage. The JAVA application
Card Handler (PC) is created in order to establish APDU communication
with a smart card via a USB interface-based reader. The application
presents the graphical user interface for the applet on a smart card.In
the zip package, you can find an executable GUI JAVA application
(Java_Card_Handler.exe) and java card applet (for java card with JCAPI
2.2.2 or newer). For more detailed instructions about the installation
and running of this program see the ReadMe.txt document inside in the
zip file.If you are interested in more info, please contact authors.
License
This
software is licensed as the closed source software under the exclusive
legal right of the copyright holder. The software is free for personal
use only. For more information about the license, please contact:Technology Transfer Office
Brno University of TechnologyE-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Software: libABC
Authors
Ing. Petr Dzurenda (dzurenda@vut.cz)
doc. Ing. Jan Hajný, Ph.D. (hajny@vut.cz)Download
It is possible to download the software here.
Read more
Project
The software was sponsored by the project GACR GP14-25298P
Description
This
software implements group signatures HM12, Schnorr Signature, Weak-BS
signature and efficient proof of knowledge of Weak-BS signature. The
software allows benchmarking of these signatures. For more info read the
manual.If you are interested in more info, please contact authors.
License
For more information about the license, please contact:
Technology Transfer Office
Brno University of TechnologyE-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Software: Android mobile application for access control system
Authors
Ing. Petr Dzurenda (dzurenda@vut.cz)
doc. Ing. Jan Hajný, Ph.D. (hajny@vut.cz)Download
To get the software, please contact IMA, s.r.o.
Read more
Project
The software was sponsored by the project TAČR TA04010476.
Description
This software implements user authentication protocols for access control systems using a mobile phone.
If you are interested in more info, please contact authors.
License
For more information about the license, please contact:
Technology Transfer Office
Brno University of TechnologyE-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Software: Smart Card Based Authentication Software
Authors
Ing. Lukáš Malina, Ph.D. (malina@vut.cz),
Ing. Petr Dzurenda (dzurenda@vut.cz),
Ing. David Smékal (smekald@vut.cz),
Ing. Jakub Konečný (xkonec58@vut.cz),
Ing. Švehlák Milan (milansvehlak@gmail.com),
Doc. Ing. Jan Hajný, Ph.D. (hajny@vut.cz),
prof. Ing. Kamil Vrba, CSc. (vrbak@vut.cz)Download
To get the free demo version for non-commercial purposes, please contact the corresponding author (Lukas Malina, email: malina@vut.cz).
To get the full version for commercial purposes, please contact the corresponding author (Lukas Malina, email: malina@vut.cz).Read more
Project
This software was financed by the Ministry of Interior under grant VI20162018003.
Description
The
software “Smart Card Based Authentication Software” implements an
advanced authentication protocol for access control systems based on
smart card platforms (Basic Cards and MultOS Cards). The authentication
protocol is based on a zero-knowledge protocol and provides strong
security level (NIST 2016-2030 and beyond). The protocol on the cards
provides 8 security versions including ECC versions (ECC up to 512b).
The user with smart cards with installed card applications can be
verified via USB card readers by the JAVA Smart card handler application
that run on PC.
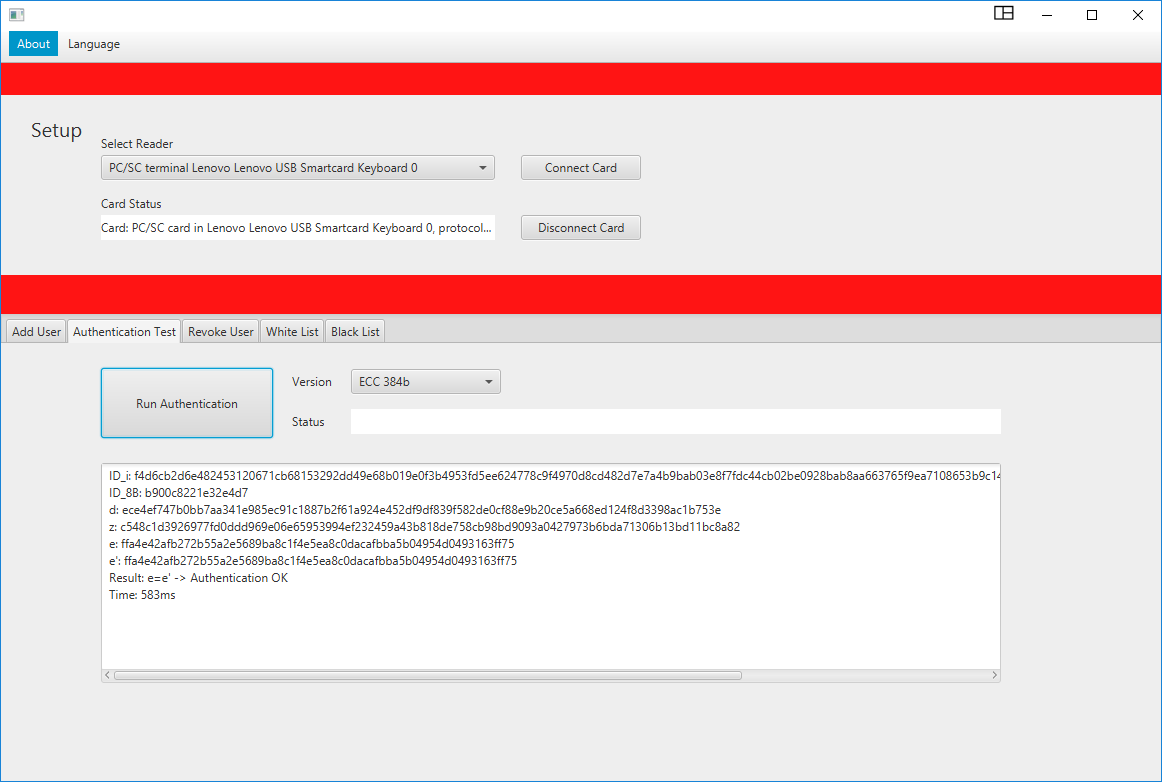
On this site, we present a description of software
that contains runnable JAVA application providing basic graphical user
interface (see a figure below) and two compiled Multos card application
(version ECC 256) for developer Multos cards. The full version is
protected under a license and is available on demand (please use the
contact email). The full version contains runnable JAVA application,
compiled Multos card applications for all versions and Basic card
application supporting all protocol versions (1024, 2048, 3072, ECC192,
ECC 224, ECC 256, ECC 384, ECC 512). For further information about card
compatibilities and GUI please read read-me files inside the SW package.
The main parts of SW package are:
– GUI JAVA application: Smart card handler application – Manager
– Basic Card application (all versions in one app) *only in full version
– Multos Card applications (two apps for v3072 and other versions)
o mvcr-ima-2017-USER-v3072.alu
o mvcr-ima-2017-USER.alu
– read me files and supported SW for upload app on the Multos CardsIf you are interested, please contact the correspond author: Lukas Malina (malina@vut.cz).
License
For more information about the license, please contact:
Technology Transfer Office
Brno University of TechnologyE-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Secure Access Module Based Authentication – Verifier Software
Authors
Ing. Lukáš Malina, Ph.D. (malina@vut.cz),
Ing. Petr Dzurenda (dzurenda@vut.cz),
Ing. Pavel Kristof (pavel.kristof@ima.cz),
Ing. Vlastimil Beneš (vlastimil.benes@ima.cz),
Ing. Jakub Frolka (frolka@vut.cz),
Ing. Tomáš Lieskovan (tomas.lieskovan@vut.cz),
prof. Ing. Kamil Vrba, CSc. (vrbak@vut.cz)Download
To get the free demo version for non-commercial purposes, please contact the corresponding author (Lukas Malina, email: malina@vut.cz).
To get the full version for commercial purposes, please contact the corresponding author (Lukas Malina, email: malina@vut.cz).Read more
Project
This software was financed by the Ministry of Interior under grant VI20162018003.
Description
The
software “Secure Access Module Based Authentication – Verifier
Software” implements an advanced authentication protocol for access
control systems that use smart cards on the user and verifier sides. The
software provides mainly the application for SAM that runs on the
verifier side and provides the necessary functionality to authenticate
users with smart cards (Basic Cards and MultOS Cards). The implemented
authentication protocol is based on the zero knowledge protocol and
provides a strong level of security (NIST 2016-2030 and beyond). The
protocol in SAM contains 8 versions for different security levels,
including ECC versions (ECC to 512b). The verifier uses the SAM module
on which the created application for the contact chip cards runs, and
through a graphical user interface application, it can authenticate a
user with a smart card. The authentication JAVA application uses the
available USB card readers and provides communication and graphical
presentation of the results during the authentication process.
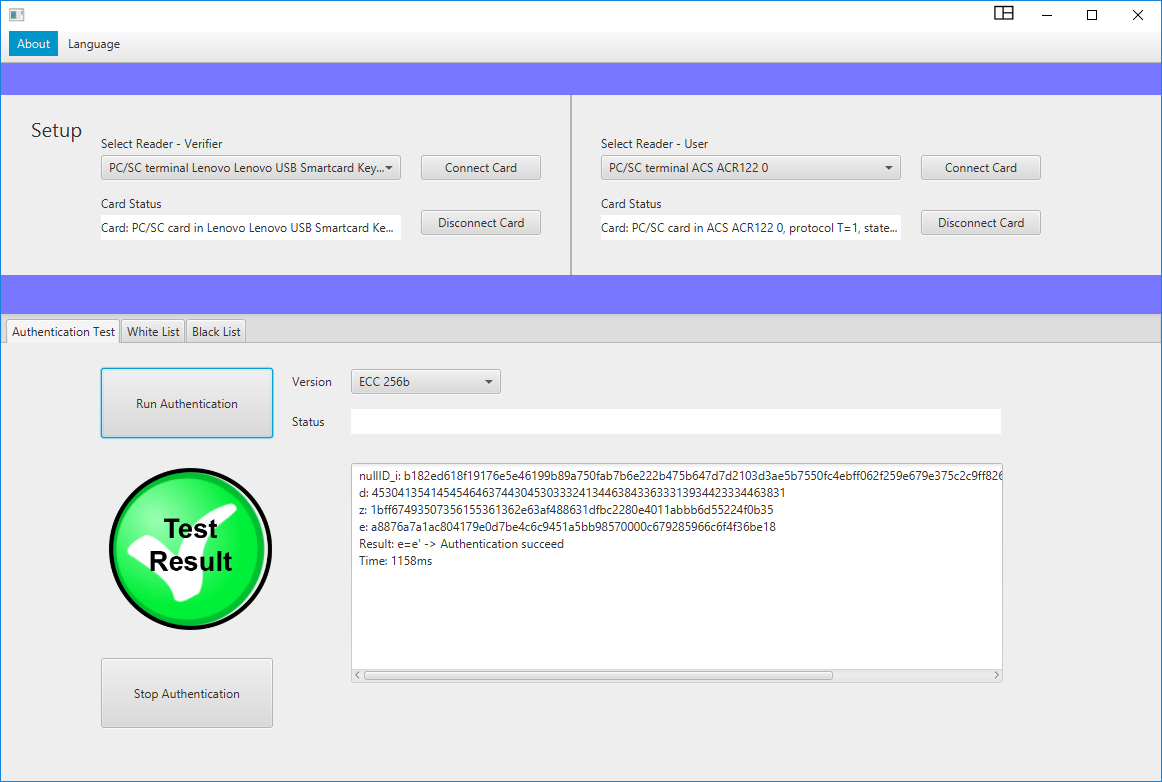
On
this site, we publish a description of software that contains runnable
JAVA application – SAM Verifier providing basic graphical user interface
(see a figure below), one compiled SAM application for Multos Cards and
two testing compiled Multos card applications for user side with
developer Multos cards. The full version is protected under a license
and is available on demand (please use the contact email). The full
version contains runnable JAVA application – SAM Verifier, compiled SAM
Multos card applications for all versions and SAM Basic card application
supporting all protocol versions (1024, 2048, 3072, ECC192, ECC 224,
ECC 256, ECC 384, ECC 512) and testing user smart card applications
(Multos and Basic). For further information about card compatibilities
and GUI please read read-me files inside the SW package.
The main parts (5 apps + readme) of SW package are:
– GUI JAVA application: SAM handler application – Verifier
– SAM Basic Card application (all versions in one app) *only in full version
– SAM Multos Card applications (two apps for v3072 and other versions)
o mvcr-ima-2017-SAM-v256.alu
o mvcr-ima-2017-SAM.alu*only in full version
– Basic Card application for a user (all versions in one app) *only in full version
– Multos Card applications for a user (two apps for v3072 and other versions)
o mvcr-ima-2017-USER-v3072.alu
o mvcr-ima-2017-USER.alu
– read me files and supported SW for upload app on the Multos CardsIf you are interested, please contact the correspond author: Lukas Malina (malina@vut.cz).
License
For more information about the license, please contact:
Technology Transfer Office
Brno University of TechnologyE-mail: info@tt.vutbr.cz
http://www.vutbr.cz/uttRead less
Symmetric encryption on the FPGA card
Authors
Ing. David Smékal (smekal@vut.cz)
Ing. Zdeněk Martinásek, Ph.D. (martinasek@vut.cz)
Ing. Lukáš Malina, Ph.D. (malina@vut.cz)
doc. Ing. Jan Hajný, Ph.D. (hajny@vut.cz)
prof. Ing. Kamil Vrba, CSc. (vrbak@vut.cz)
Ing. Denis Matoušek (matousek@netcope.com)Download
To get the software, please contact Netcope Technologies, a.s. (info@netcope.com).
Read more
Project
This software was financed by the Ministry of Interior under grant VI20162018036.
Description
The
software implements the AES (Advanced Encryption Standard) algorithm
for FPGAs (Field Programmable Gate Array) in the VHDL (Hardware
Description Language) programming language. The software contains of the
cryptographic core of the AES algorithm using a 128-bit key in GCM mode
(Galois/Counter Mode). This implementation is based on the 4 duplicated
encryption cores and employs pipelined processing in order to achieve
full 100 Gbps encryption speed. The design is implemented and verified
on the acceleration card NFB-100G2Q.If you are interested, please contact the correspond author: Zdeněk Martinásek (martinasek@vut.cz).
License
For more information about the license, please contact:
To get the software, please contact Netcope Technologies, a.s. (info@netcope.com).
Read less
Hardware cryptographic demonstrator
Authors
Ing. David Smékal (smekald@vut.cz)
Ing. Petr Jedlička (xjedli23@vut.cz)
doc. Ing. Lukáš Malina, Ph.D. (malina@vut.cz)
Ing. Pavel Šeda, Ph.D. (sedap@vut.cz)
Ing. Patrik Dobiáš (xdobia13@vutbr.cz)
prof. Ing. Kamil Vrba, CSc. (vrbak@vut.cz)
Ing. Peter Cíbik (xcibik00@vutbr.cz / cibik@magmio.com)
Ing. Jakub Hrabovský (hrabovsky@magmio.com)Download
To get the software, please contact MAGMIO, a.s. (info@magmio.com).
Read more
Project
This software was financed by the Ministry of Interior under grant VI20192022126.
Description
The software represents a library of cryptographic primitives for the FPGA platform as P4 externs (short name: Hardware cryptographic demonstrator; designation: CRYPTOACCEL). It is an implementation of all basic cryptographic mechanisms (i.e. symmetric block ciphers, asymmetric digital signature, hash function and postquantum digital signature) on the FPGA platform in VHDL (VHSIC Hardware Description Language) so that they can be used modularly as externs in language P4, which will allow them to be easily used even by users lacking experience in hardware development, without a negative effect on the performance of the implementation.
If you are interested, please contact the correspond author: Lukáš Malina (malina@vut.cz).
License
For more information about the license, please contact:
To get the software, please contact Magmio, a.s. (info@magmio.com).
Read less
Cryptographic objects as externs in Netcope P4 compiler
Authors
Ing. Peter Cíbik (xcibik00@vutbr.cz / cibik@magmio.com)
Bc. Petr Ohnút (ohnut@magmio.com)
Mychajlo Novikov (novikov@magmio.com)
Ing. Jakub Hrabovský, Ph.D. (hrabovsky@magmio.com)Download
To get the software, please contact MAGMIO, a.s. (info@magmio.com).
Read more
Project
This software was financed by the Ministry of Interior under grant VI20192022126.
Description
The software represents a solution for support of various cryptographic objects as P4 externs in Netcope P4 compiler. The solution provides the interface specification and implementation of top modules as well as wrappers in VHDL (VHSIC Hardware Description Language) for each of the common cryptographic primitives (symmetric cipher AES-GCM-256, asymmetric digital signature EdDSA, keyed-hash message authentication code HMAC-SHA3-512, hash functions SHA3-256 and SHA3-512) in order to integrate them into P4 pipeline through Netcope P4 compiler. Furthermore, this extension allows users to integrate their own implementations of various cryptographic primitives into Netcope P4 compiler in the form of cryptographic externs, which can be then directly used in P4 source code.
If you are interested, please contact the Magmio a.s. (info@magmio.com).
License
For more information about the license, please contact:
To get the software, please contact Magmio, a.s. (info@magmio.com).
Read less
Verification framework for user systems with integrated cryptographic P4 externs
Authors
Ing. Peter Cíbik (xcibik00@vutbr.cz / cibik@magmio.com)
Bc. Petr Ohnút (ohnut@magmio.com)
Mychajlo Novikov (novikov@magmio.com)
Ing. Jakub Hrabovský, Ph.D. (hrabovsky@magmio.com)Download
To get the software, please contact MAGMIO, a.s. (info@magmio.com).
Read more
Project
This software was financed by the Ministry of Interior under grant VI20192022126.
Description
The software represents a set of tools for automatic verification of FPGA firmware created by Netcope P4 compiler in the translation process of user P4 source code, which contains any of the supported cryptographic externs. Verification framework supports all common cryptographic primitives (symmetric cipher AES-GCM-256, asymmetric digital signature EdDSA, keyed-hash message authentication code HMAC-SHA3-512, hash functions SHA3-256 and SHA3-512). Framework includes a tool for automatic generation of testing samples exported into pcap files with the usage of reference implementations of related cryptographic functions, a tool for detailed comparison of various samples, a tool for automatic build of FPGA firmware, and main tool for automatic functional verification of FPGA firmware directly in the FPGA card. Verification of any custom system with cryptographic externs in P4 becomes simple by the application of the listed tools included in the framework without a need for any knowledge of FPGA technology
If you are interested, please contact the Magmio a.s. (info@magmio.com).
License
For more information about the license, please contact:
To get the software, please contact Magmio, a.s. (info@magmio.com).
Read less
Secure Cloud Storage System for Digital Evidence (CSDE)
Authors
Ing. Petr Muzikant (xmuzik08@vut.cz)
doc. Ing. Lukáš Malina, Ph.D. (malina@vut.cz)
Ing. Petr Dzurenda, Ph.D. (dzurenda@vut.cz)
doc. Ing. Jan Hajný, Ph.D. (hajny@vut.cz)
RNDr. Antonín Dufka (445281@mail.muni.cz)
doc. RNDr. Petr Švenda, Ph.D. (xsvenda@fi.muni.cz)
Mgr. Václav Stupka, Ph.D. (stupka@ics.muni.cz)
Download
To get the access to the system, please contact VUT AXE (axe@vut.com).
To get the source codes for a non-commercial purpose, please go to: https://gitlab.com/brno-axe/mvcr-dect/dect-nextcloud-docker
Read more
Project
This software was financed by the Ministry of Interior under grant VJ01010084.
Description
Software entitled Secure Cloud Storage System for Digital Evidence (CSDE) represents a new secure storage system for preserving electronic evidence. The system integrates a number of created submodules and an extension of the cloud open-source platform Nextcloud, which has been programmatically modified and expanded. These extensions were created to transform the basic version of Nextcloud into a specialized storage for electronic evidence. The expanding submodules enhance access security, ensure the long-term integrity of stored data, and apply modern cryptography (multi-party signatures, post-quantum cryptography).
If you are interested, please contact AXE (axe@vut.com).
License
For more information about the license, please contact: AXE (axe@vut.com).
To get the software, please contact AXE (axe@vut.com).
Read less
Android mobile app for accessing a shared vehicle (IMA CARSHARING)
Authors
Ing. Petr Dzurenda, Ph.D. (dzurenda@vut.cz)
doc. Ing. Lukáš Malina, Ph.D. (malina@vut.cz)
Ing. Petr Ilgner (ilgnerp@vut.cz)
Ing. Minh Tran (xtranm00@vut.cz)
Ing. Vlastimil Beneš (vlastimil.benes@ima.cz)
Ing. Pavel Krištof (Pavel.Kristof@ima.cz)
Ing. Anatolij Makarov (anatolij.makarov@ima.cz)Download
To get the software, please contact VUT AXE (axe@vut.com) or IMA, a.s. (vlastimil.benes@ima.cz).
Read more
Project
This software was financed by the Technology Agency of the Czech Republic under the grant agreement No. CK03000040 (Protection of data flows in shared means of transport).
Description
The software represents a mobile application for the Android OS. This application is part of the developed and implemented ProDaTran system solution designed for managing and sharing vehicles within corporate vehicle fleets. The application allows the user to communicate with ProDaTran online servers (managed by IMA) that ensure the management of user digital identities and vehicle reservation management. After its registration (activation at the ProDaTran server for managing user digital identities), the application allows the user to download vehicle reservations from the ProDaTran server for managing vehicle reservations. Thanks to the data downloaded during each reservation, the user can unlock or lock the vehicle offline (i.e. without the need for an Internet connection). The cryptographic core of the authentication protocol for accessing the vehicle is designed to have minimal data transfer requirements and minimal computing and memory requirements for the vehicle unit.
If you are interested, please contact AXE (axe@vut.com).
License
For more information about the license, please contact: AXE (axe@vut.com).
To get the software, please contact AXE (axe@vut.com) or IMA, a.s. (vlastimil.benes@ima.cz).
Read less